Phishing, Whaling Phishing, and Spear Phishing – What you Need to Know:
Phishing is any type of email attack that tries to fool a victim into taking some action. The term ’phishing’ is a spin on the word fishing, because these criminals are dangling a fake ’lure’ (the email and website look legitimate) hoping users will ’bite’ by providing their information. This includes sharing sensitive information, such as usernames, passwords and financial records for malicious purposes; installing malware; or completing a fraudulent financial payment or wire transfer.
While ordinary phishing attacks usually involve sending emails to a large number of individuals without knowing how many will be successful, there are also attacks called “whaling phishing attacks.” These usually target one specific individual at a time — typically a high-ranking individual — with highly personalized information.
A whaling attack is a special form of spear phishing that targets specific high ranking victims within a company. Spear phishing attacks are even more aimed, and can target any specific individual. Both types of attack generally require more time and effort on the part of the attacker than ordinary phishing attacks.
Macro Embedded Emails:
If you receive a PDF, Excel, Word, or other document which asks for an activation, enabling, macros, or other popup for editing, please use caution. This is the most common method for ransomware delivery. Upon activation, the software will silently download itself, and run without being noticed. This will result in encryption of all files made available to the software both locally and over shared drives.
What increases risk?
- Malware Infection (Active or Past/Cleaned) often results in entire address books being harvested. This makes it easier for targeting important members by having an actual email address list.
- Public Profiles: Having your accounts, names, positions, and place of work on public sites does increase your risk of target. Linked-In is an example of a site that does provide details which allow for these criminals to better engineer a potential target.
- Security Breaches: This occurs when a company that has your information suffers a security breach, your personal information such as email, name, or other indefinable information becomes available for use.
- Acknowledgements: If you reply to spam or malicious email, you may become a target as they now have a confirmed inside response.
How can I tell if an Email is a Scam?
Luckily, there are often telltale signs an email is a scam. Here are a few things to look out for:
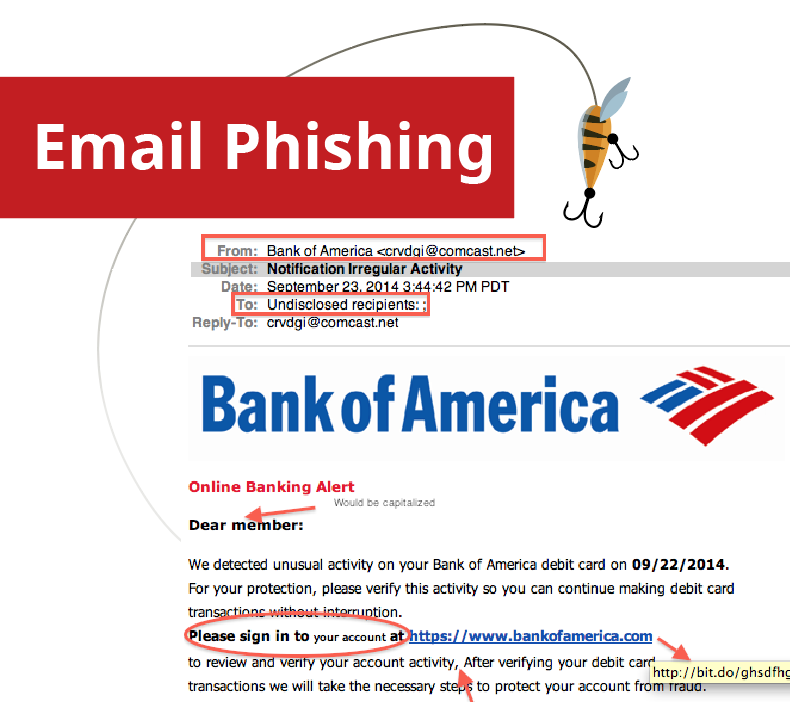
- The email is not addressed to the recipient. (Often lines like “Dear Customer”, “Dear User” are used in place of your name – any company that is legitimate will have your name on file and address you accordingly in your email).
- Action was not taken. Sometimes these scam emails will say you have exceeded login attempts, reset a password, or account action is required – these cases make it very obvious they are not legitimate because you have not taken those actions on their website.
- Grammatical errors. Scam emails are often riddled with spelling and grammar errors, be on the look-out for these issues as they are usually a telltale sign. (example image below has many grammar errors and uses strange wording).
- Multiple Links. These emails typically contain multiple links to websites that are not what they are pretending to be. For example, their link may say https://truewebsite.com but the actual location it takes you to is https://scamwebsite.com; You can often hover over a link in an email to see if there is a redirect.
- From Email is Suspicious. The sender/from email usually looks “off” often using a similar name for who they want to be perceived as in their email address. For example: someone may try to come off as the University of Chicago and use sender@uchicago.com where a legitimate email for any university always ending in .edu, for example sender@uchicago.edu.

At QSG your email is protected by a high quality spam filtering service which reduces the level of junk mail in your inboxes.We are testing new mitigation methods and services for this specific attack structure. Despite the best defenses, we believe that proper notification of users helps increase the success rate for protection. Our services filter out a minimum of 99% of malicious email and all attempts are made to utilize industry respected sources. Recommendations to improve security have to be made on a case by case basis as a result of each target market, organization, industry, and organization size result in a different type of attack prevalence.For increased security, please be on the look-out for any suspicious emails and contact us if you have any doubts. When it comes to phishing attempts it is always better safe than sorry.

